
Introduction: What is ‘The Hack’? In recent weeks, the cybersecurity community has been shaken by a significant incident known as ‘The Hack’. This breach has brought to light the vulnerabilities that exist within digital ecosystems, highlighting the importance of strong cybersecurity measures for individuals and organisations alike. As our dependence on technology increases, understanding such

Introduction The security of our online accounts is paramount, especially with the increasing number of data breaches in recent years. One such incident that has emerged is the recent Gmail passwords data breach, underlining the vulnerabilities associated with even the most trusted email services. The relevance of this breach cannot be overstated, as it raises
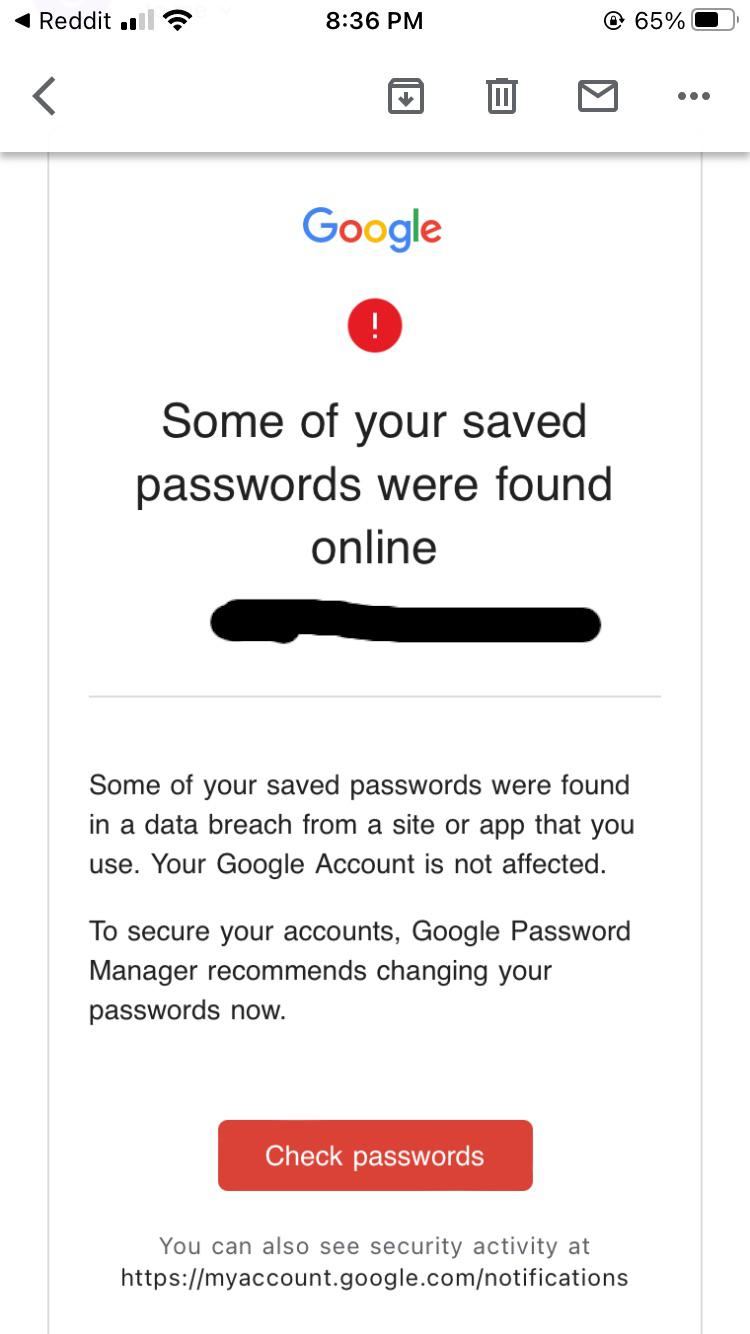
Introduction The security of personal information has never been more critical, particularly with the increase in cyber threats targeting online accounts. Recently, the world faced yet another wake-up call with a significant Gmail passwords breach that has raised eyebrows and, more importantly, concerns about data privacy. With millions of users relying on Gmail for personal

Introduction The Lazarus group, associated with North Korea, has garnered global attention for its sophisticated cyberattacks. As cyber security threats escalate, understanding the operations of this notorious group becomes crucial for governments and businesses alike. The term “Lazarus” is not only synonymous with the biblical figure who was raised from the dead but also represents

Introduction The Lazarus Group, believed to be affiliated with the North Korean government, has become one of the most notorious cyber attack groups in recent years. With a significant reputation for sophisticated cyber espionage and theft, documenting their activities has grown increasingly important as their reach expands globally. Recent events have highlighted their evolving tactics,

Introduction In an age of rapid digital transformation, the threat posed by hackers has surged, raising alarms for individuals, companies, and governments alike. Cybersecurity is now among the foremost concerns for organisations across all sectors, as breaches can lead to significant financial losses, reputational damage, and threats to national security. Understanding the dynamics of hacking
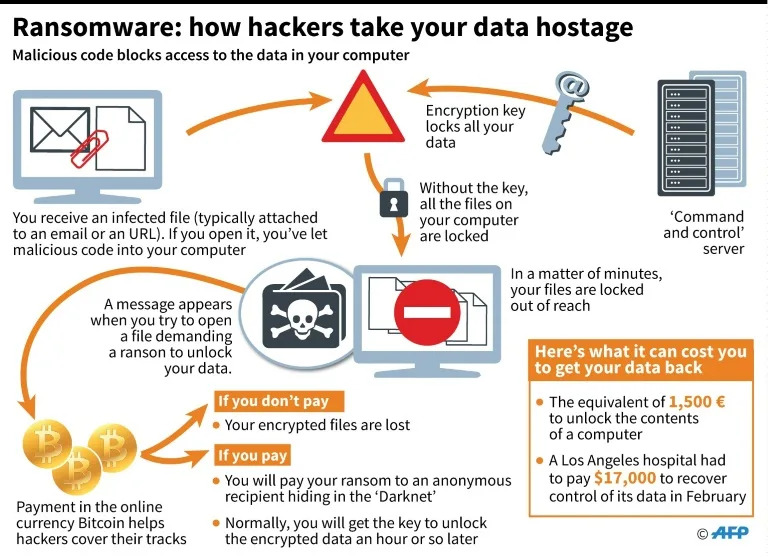
Introduction In today’s digital era, corporate security is paramount, and the recent cyber attack on Renault has underscored the vulnerabilities even major automotive manufacturers face. As a global leader in the automotive industry, Renault’s operations and confidential data are critical not only to the company but also to its stakeholders and customers. The attack raises

Introduction to the Cyber Attack The recent cyber attack on Jaguar Land Rover (JLR), one of the UK’s leading automotive manufacturers, has raised critical concerns regarding data security and the operational resilience of major corporations. As cyber threats become increasingly sophisticated, the incident underscores the vulnerability of even the most reputable brands in the face

Introduction The topic of cyberattacks has risen to the forefront of global discussions following a recent high-profile hack that exposed sensitive data and disrupted operations across various sectors. The implications of this event underline the increasing vulnerabilities companies face in the digital age, highlighting the urgent need for robust cybersecurity measures. With cyberattacks becoming more

Introduction The significance of airport security has escalated in recent years, with digital threats becoming a prime concern. Recent reports indicate that Heathrow Airport is facing an uptick in cyber attacks, raising alarms about the vulnerability of crucial transport hubs. As one of the busiest airports in the world, the safeguarding of Heathrow from cyber