
Introduction to Zero-Day Vulnerabilities In the ever-evolving landscape of cybersecurity, the term ‘zero-day’ has emerged as a significant concern for both individuals and organisations. Zero-day vulnerabilities are security flaws in software that are exploited by attackers before they are known to the software developer or the general public. The relevance of understanding zero-day attacks has

Introduction to Zero-Day Vulnerabilities In the realm of cybersecurity, zero-day vulnerabilities represent one of the most pressing threats faced by individuals and organisations alike. These vulnerabilities refer to flaws in software that are unknown to the vendor and, crucially, have not yet been patched. The term ‘zero-day’ indicates that developers have had zero days to
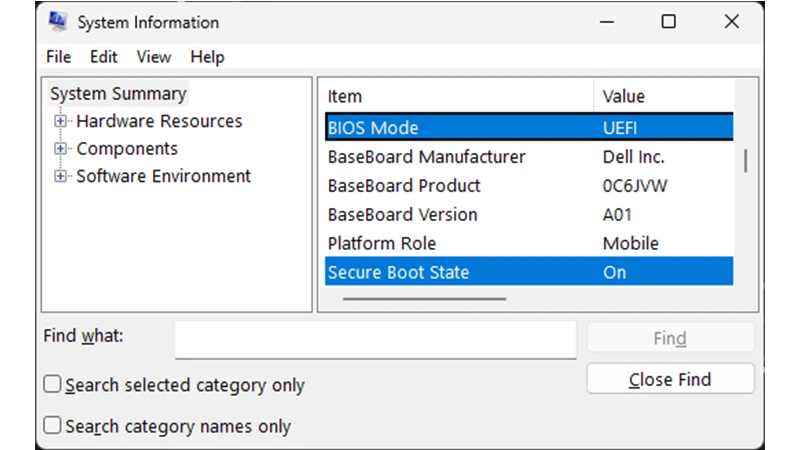
Introduction to EA Secure Boot EA Secure Boot has gained significant attention as an essential mechanism for ensuring the integrity of devices and systems in today’s technology-driven world. In an age where cyber threats are increasingly sophisticated, the importance of secure boot processes cannot be overstated. They play a critical role in preventing unauthorised access

Introduction In the world of cybersecurity, the discovery of vulnerabilities can have significant implications for both individuals and organisations. The Spectre vulnerability, first reported in January 2018, is one of the most critical security threats that affects modern processors. It exploits flaws in how speculative execution works in CPUs, leading to potential data breaches. Understanding
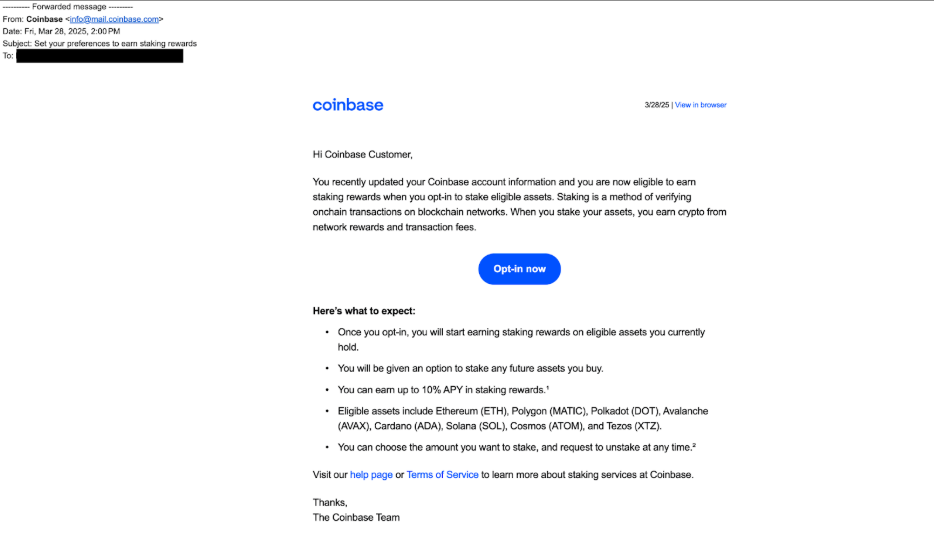
Introduction As cryptocurrency continues to gain popularity, so do the threats associated with it. Recent reports indicate a surge in Coinbase email scams, which have targeted users of the leading digital currency exchange platform. These scams are crucial to address, as they not only put individuals’ finances at risk but also jeopardize the integrity of

Introduction EncroChat has emerged as a significant force in the realm of secure communications, particularly among criminal networks. Initially marketed as a privacy-focused messaging service, it gained notoriety for its use in coordinating illicit activities across Europe. With its sophisticated encryption and user-friendly design, EncroChat appealed to individuals seeking confidentiality in their communications. However, its

Introduction to EncroChat EncroChat, a secure communication platform originally designed for privacy-conscious users, has recently garnered significant attention due to its role in law enforcement operations across Europe. With growing concerns over online privacy and security, the app offers encrypted messaging services, making it popular among users seeking anonymity. However, its use has raised critical

The Importance of Tor In an increasingly digital world where online privacy is constantly under threat, the Tor network remains a vital tool for anonymity. Launched in the early 2000s, Tor (The Onion Router) was initially developed by the United States Navy for secure communications. Today, it serves as a crucial resource for users seeking

Introduction EncroChat, a secure communications platform known for its use among criminals, became a significant part of law enforcement’s strategies in combating organised crime. Its importance has surged in the UK, especially after police operations successfully infiltrated this encrypted network, leading to numerous arrests and the disruption of various criminal activities. The ramifications of EncroChat

Introduction to Spectre The Spectre vulnerability, first disclosed in January 2018, has revolutionised the landscape of cybersecurity. As a flaw that affects modern microprocessors, Spectre has been a pivotal topic due to its implications for data security and privacy. With the increasing reliance on digital infrastructure for both personal and professional contexts, understanding Spectre and