
Introduction to Zero Day Vulnerabilities
Zero day vulnerabilities represent a severe threat in the realm of cybersecurity. These security flaws are called ‘zero day’ because they are exploited before the software developer has had a chance to release a fix. As such, the term captures the urgency associated with these vulnerabilities, which often leave systems exposed to hackers and malicious attacks. The topic has escalated in importance due to increasing reports of cyber attacks targeting everything from personal devices to large corporate infrastructures.
Recent Examples and Incidents
In September 2023, a widely reported zero day vulnerability was identified in a popular web browser. Cybersecurity experts revealed that an exploit was actively being used by attackers to gain unauthorized access to user data. The developers acted quickly, but the incident highlighted how quickly these vulnerabilities can be exploited in the wild. In another example, a zero day vulnerability in a major operating system was discovered, which could allow attackers to take control of affected devices. These incidents underscore the critical need for security patches and user awareness.
The Lifecycle of Zero Day Vulnerabilities
The lifecycle of zero day vulnerabilities can be divided into several stages: initial discovery by a hacker, exploitation in the wild, and eventual patch release by the software vendor. Unfortunately, once a zero-day exploit is made public or is discovered by developers, it can lead to widespread attacks before users can properly protect themselves. The race between cybercriminals and developers to either exploit or patch vulnerabilities adds a significant layer of complexity to cybersecurity protocols.
The Broader Impacts of Zero Day Vulnerabilities
Professionally, zero day vulnerabilities can lead to severe financial damages, reputational harm, and legal consequences for businesses. For consumers, the risks involve not just financial loss but also theft of personal information or dangerous breaches that can compromise their privacy and security online. The collective fear of these vulnerabilities has led individual users, as well as businesses, to enhance their cybersecurity measures, including regular updates and the implementation of robust security protocols.
Conclusion and Future Considerations
As technology continues to evolve, zero day vulnerabilities will remain a pressing concern in the landscape of cybersecurity. It is essential for both users and organizations to stay informed about potential threats, implement best security practices, and encourage timely updates to reduce vulnerability exposure. Looking ahead, ongoing education and awareness will be paramount in combating these silent but dangerous threats. Furthermore, advancements in AI and machine learning could play a significant role in identifying and mitigating zero day vulnerabilities before they can be exploited.
You may also like

What You Need to Know About ‘The Hack’ Cybersecurity Incident
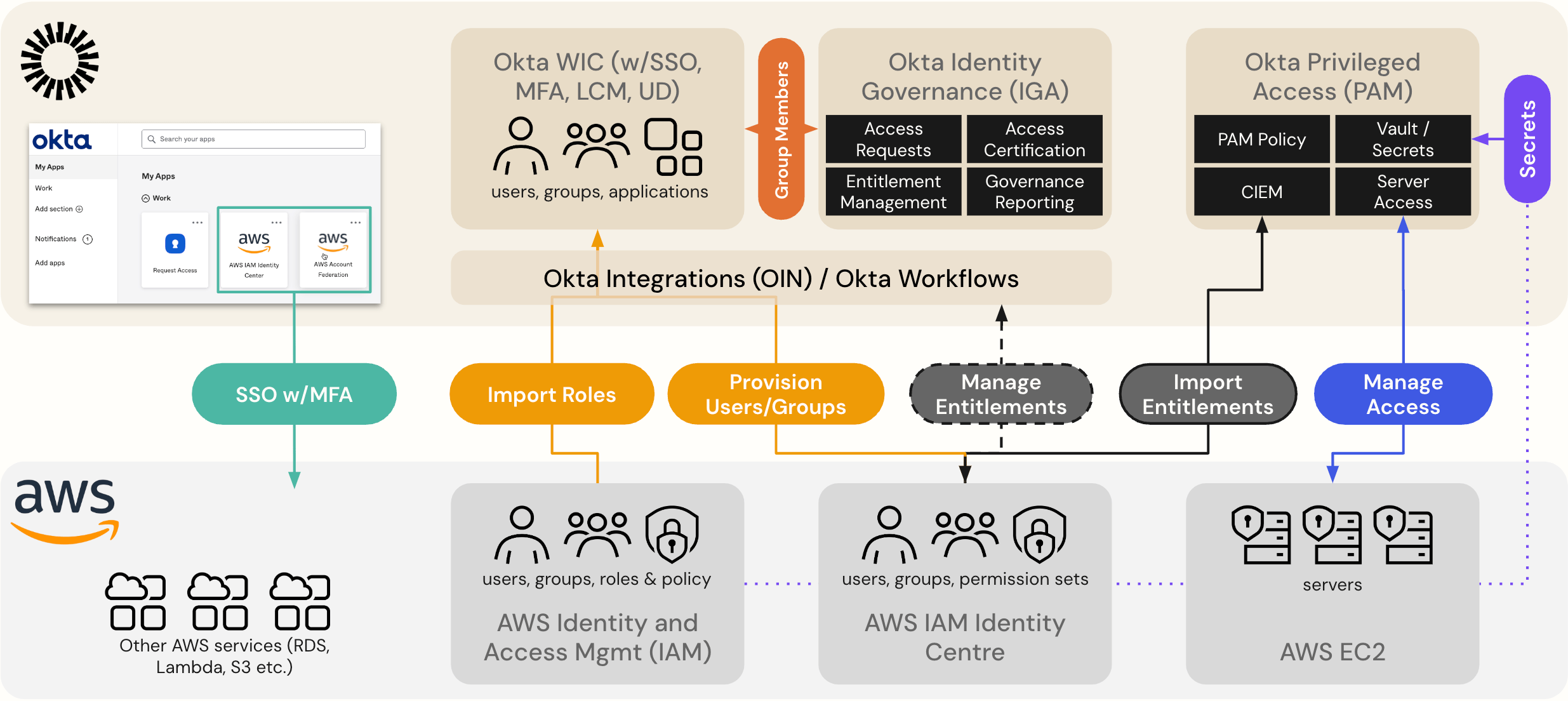
The Significance of Okta in Modern Identity Management

Recent Gmail Passwords Data Breach: What You Need to Know
SEARCH
LAST NEWS
- Remembering Wendy Richard: The Promise to Co-Star Natalie Cassidy
- How Did Anglian Water Achieve an ‘Essentials’ Rating for Mental Health Accessibility?
- Shai Hope Leads West Indies in T20 World Cup Clash Against South Africa
- What We Know About Weston McKennie: Future at Juventus and Past at Leeds
- What We Know About the Upcoming Live Nation Antitrust Trial