
Introduction to Zero-Day Vulnerabilities
In the realm of cybersecurity, zero-day vulnerabilities represent one of the most pressing threats faced by individuals and organisations alike. These vulnerabilities refer to flaws in software that are unknown to the vendor and, crucially, have not yet been patched. The term ‘zero-day’ indicates that developers have had zero days to address the issue, leaving systems exposed to potential attacks. With the ever-increasing reliance on technology for daily operations, understanding and mitigating the risks associated with zero-day vulnerabilities has become more critical than ever.
Recent Events Highlighting Zero-Day Threats
In 2023, several high-profile incidents have underscored the dangers posed by zero-day vulnerabilities. In June, cybersecurity researchers discovered a zero-day flaw in the Microsoft Windows operating system that allowed attackers to gain elevated permissions. This vulnerability was exploited in the wild, enabling malicious actors to take control of affected systems. Soon after, evidence surfaced that state-sponsored hacking groups had targeted critical infrastructure, leveraging unpatched zero-day vulnerabilities to breach systems.
Moreover, prolific software vendors like Google and Apple have also had to respond promptly to emerging zero-day threats. In July, Google issued an emergency security update to address a zero-day in its Chrome browser, which was found to be actively exploited. Such incidents highlight how quickly the cyber landscape can shift and the necessity for organisations to maintain robust security protocols.
The Importance of Vigilance and Protection Measures
Protecting against zero-day vulnerabilities requires a multi-layered approach. Regular software updates, robust intrusion detection systems, and employee training on cybersecurity best practices are essential. Additionally, threat intelligence services can provide early warning alerts about new vulnerabilities and active attacks, allowing systems to be fortified proactively before they can be exploited.
Conclusion: The Future of Cybersecurity
As technology continues to evolve, so do the tactics deployed by cybercriminals. The threat of zero-day vulnerabilities will likely remain a significant concern for the foreseeable future. It is imperative that both individuals and organisations remain vigilant, enact comprehensive security strategies, and foster an environment where cybersecurity is prioritised. Looking ahead, investment in research and development for more advanced detection and prevention technologies will be critical to safeguard against the ever-present threat of zero-day vulnerabilities.
You may also like

What You Need to Know About ‘The Hack’ Cybersecurity Incident
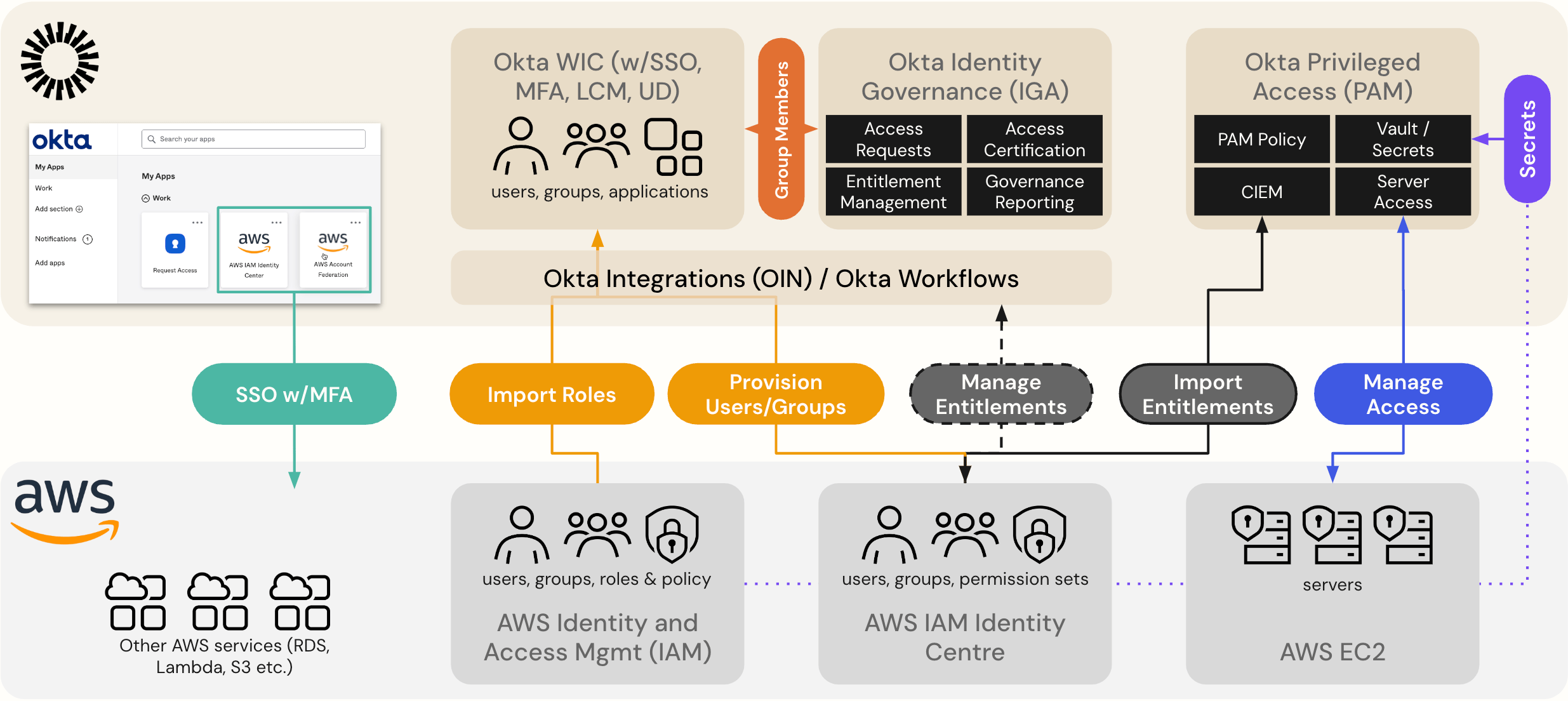
The Significance of Okta in Modern Identity Management

Recent Gmail Passwords Data Breach: What You Need to Know
SEARCH
LAST NEWS
- Remembering Wendy Richard: The Promise to Co-Star Natalie Cassidy
- How Did Anglian Water Achieve an ‘Essentials’ Rating for Mental Health Accessibility?
- Shai Hope Leads West Indies in T20 World Cup Clash Against South Africa
- What We Know About Weston McKennie: Future at Juventus and Past at Leeds
- What We Know About the Upcoming Live Nation Antitrust Trial