
Introduction
Zero day vulnerabilities are critical security flaws in software that are exploited by cybercriminals before the vendor has released a patch. With increasing reliance on technology, the significance of understanding these vulnerabilities is paramount, as they pose a significant threat to individuals, businesses, and national security.
Recent Incidents
In 2023, several high-profile zero day vulnerabilities have made headlines, impacting popular software and causing severe repercussions. For example, the recent zero day exploit in Microsoft Exchange Server was discovered in August, allowing attackers to bypass authentication and gain unauthorized access to sensitive information. This incident resulted in numerous breaches across various industries, highlighting the urgency for organizations to enhance their cybersecurity measures.
Moreover, the vulnerability found in Google Chrome in September has raised concerns among users worldwide, forcing Google to expedite its security updates to mitigate potential damage. This incident underscores the constant cat-and-mouse game between cybercriminals and software developers, where timely updates and patches are crucial for maintaining system integrity.
The Importance of Awareness and Prevention
The implications of zero day vulnerabilities extend beyond immediate data breaches. They can lead to long-term reputational damage, financial loss, and regulatory consequences for affected organizations. Businesses are urged to implement robust security policies, conduct regular vulnerability assessments, and invest in advanced threat detection systems to safeguard against such exploits.
Conclusion
The threat of zero day vulnerabilities is ever-present, necessitating a proactive approach to cybersecurity. As software becomes more complex and integrated into everyday life, the risk of encountering zero day exploits increases. By staying informed of the latest threats and prioritising cybersecurity measures, individuals and organisations can better protect themselves against these insidious risks, ensuring a more secure digital environment.
You may also like

The Rising Threat: An Overview of Modern Dangers

What You Need to Know About ‘The Hack’ Cybersecurity Incident
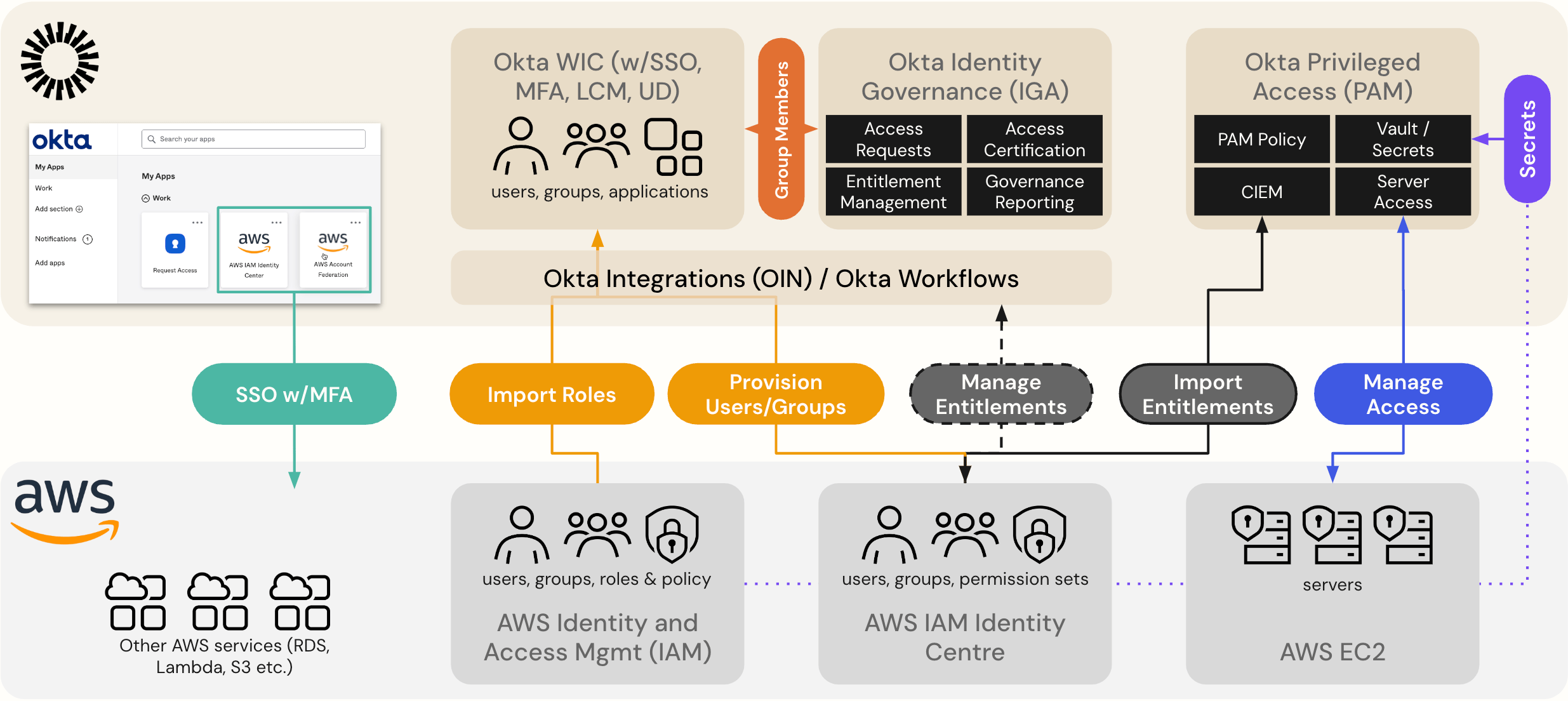
The Significance of Okta in Modern Identity Management
SEARCH
LAST NEWS
- Remembering Wendy Richard: The Promise to Co-Star Natalie Cassidy
- How Did Anglian Water Achieve an ‘Essentials’ Rating for Mental Health Accessibility?
- Shai Hope Leads West Indies in T20 World Cup Clash Against South Africa
- What We Know About Weston McKennie: Future at Juventus and Past at Leeds
- What We Know About the Upcoming Live Nation Antitrust Trial